If it looks like a phish & smells like a phish, don’t be entirely surprised if your connection request gets reported to LinkedIn, your profile blocked and I decide to publically dissect things a bit (or should that be fillet?) for this months blog post.
Perhaps there was a genuine human being behind the initial request, but if so then in this particular case I suspect their intentions may have been, shall we say, less than honourable.
So let’s rolls up our sleeves & off we go…
Step 1: An Unsolicited or Cold Approach.
OK, there’s nothing strictly wrong with that (your mileage may vary, naturally). It can be part and parcel of many a prospect-to-lead sales exercise.
Until relatively recently I’ve leaned towards only accepting LinkedIn contact requests from people I’ve met either in person or online. Potentially limiting, yes, but at least there’s been some form of human / not human validation process.
Problem is it’s getting harder, what with generative AI and other technology blurring the lines. Still, best efforts all round.
If my tone, either written or in person, ever does occasionally come across as somewhat professionally brusque, diplomatic or stand-offish I hope you don’t take it as a personal affront.
“Who are you and what do you want?” are perfectly valid questions.
If we haven’t been introduced through a trusted other (actually as far as I’m concerned it is particularly valid if we haven’t) it’s probably what’ll be foremost in my mind.
Many of us are in sales, from a certain point of view, so I want to find out whether you’re selling, buying, perhaps a bit of both… or something else altogether.
Please don’t get me wrong. I’m still probably interested in finding out what it is you have to say, if only because I’m likely evaluating your approach from a critical but professional perspective.
For example:
- How do you approach sales conversations?
- Can I learn something from you? Something new? How to do something better?
- Can I learn what not do from you?
- How have you tried to catch & hold my attention?
- Is it working?
- Why / why not?
- What else?
- What next?
And of course: “Who are you and what do you want?“
Most of the time I’ll look to enquire as to whether there’s anything I may be able to help you with.
“Hi, how can I help you?”
It’s a warmer and more welcoming tone in my opinion. People are interesting creatures and everyone’s got a story to tell.
If I’m feeling a bit mischievous I may couch my language as follows:
“Hello… what is you think I can do for you?”

Step 2: An image of a seemingly interested young woman.
Perhaps you are. Whilst I’m no John le Carré but I’ve seen & read enough “stale beer spy fiction” to have heard of this one.
See also: ‘honeytrap’, ‘lure’, ‘bait’, ‘decoy’, ‘schmuck’, ‘sucker’, ‘gullible idiot’ etc.

OK this requires a bit of unpacking & additional context.
I was brought up to, on the whole, take people as I find them. To not jump to conclusions. Not to be quick to judge a person when meeting someone. To remember that all people hold the intrinsic value of being another human being.
By and large this remains true. I rather like meeting new people. I often enjoy the networking side of business development. It can be taxing at times, but it is always interesting.
The thing is that none of us can afford to be credulous, gullible, naïve or otherwise susceptible to the predations of certain others out there.
Nobody wants to be taken advantage of, so be mindful and take a balanced, sensible approach towards things so that you minimise the chances of becoming a victim of deceipt, fraud or a con.
See also: ‘mark’, ‘rube’, ‘mug’, ‘schmuck’, ‘chump’, ‘fool’, ‘dupe’, ‘patsy’, ‘sucker’ etc.

Step 3: Interesting job title, big brand name.
To quote Michael Palin from a sketch in the film ‘Monty Python’s: The Meaning of Life’:
“Gosh, we’re all really impressed down here, I can tell you.“
Joking aside whatever your position, job title, station or sobriquet in life then if you’ve honestly earned it then I’m happy for you. Really. It’s testament how hard you’ve worked and you deserve recognition, credit and plaudits. Go you!
Alternatively if it’s an accident of birth, happenstance, an affectation or deliberate misinformation designed to exploit, entangle or manipulate I’m probably going to be somewhat more… temperate in my response.
Let’s try not to forget that we’re all cut from a very similar cloth. We’re all human beings, we’re all fallible and we’re all hanging on to this island earth as it hurtles through the cosmos.
The journeys the interesting bit, but we’re all heading towards the same destination. Still… we can have some fun along the way, right?
I’m a company director because I founded a limited company & that’s what Companies House considers me to be. I’m a consultant because I want to help you manage how you as business owner, director, leader or decision maker make better use of information.
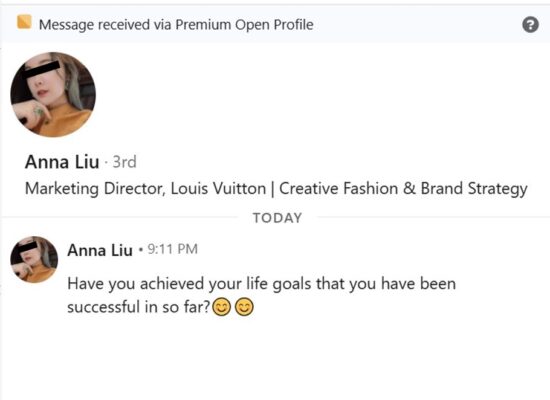
Step 4: Somewhat vague, non-committal opener.
“Have you achieved your life goals that you have been successful in so far?” Smiley face, smiley face.
Deliberately generic question intended to solicit engagement, or AI generated or otherwise nebulous schlock? I don’t know for certain, but at this point I’m way beyond the point of interacting with this opener (other than to see what else I can glean from this presumed phishing attempt & make use of it in this months blog post).
By this point in the process I already know that:
- I’m not going to accept this connection request
- It’s almost certainly a phishing attempt
- I’m going to use LinkedIn’s inbuilt tools to both report & block this
Total time elapsed from seeing this connection request in LinkedIn? Probably less than ten (10) seconds from first viewing it to rejecting it.
I’ve spent far more time writing this blog post than I did on assessing the connection attempt, but at the very least I’m getting something out of it.

So what did I do next?
I took stock of the facts and considered the following:
- The security aspect of my professional interest has been piqued
- ‘Due diligence’ is a hallmark of professionalism
- I’ve still got to write May’s blog post
Time to do a bit of investigative research.
A search across a range of image lookup sites online suggested the profile image was been copied from a dating website based in Russia.
Hmm.
Of course this doesn’t mean the phishing attempt actually originates from there… I mean it might, but proxy servers are a thing after all.
This isn’t the first time this kind of thing has happened to me through LinkedIn. I certainly don’t expect it be the last and it should serve as a reminder to all of us to be vigilant, validate our contacts to the best of our abilities and take reasonable steps to keep data, information and knowledge protected.
Out on what used to be known in days of yore as the “information superhighway” there are all kinds of bandits, highwaymen (and women), brigands, rogues, ne’er do wells, rascals and all kinds of just plain downright wrong ‘uns.
In my almost half a century of kicking around this planet we call Earth it’s been my experience that, most of the time, most people genuinely are trying to make an honest connection.
It may be business related or otherwise and that’s fine. It’s more than fine, honestly. People generally gravitate towards other people… and why not? Most folk are relatively social and sociable creatures and, well, people can be fascinating.
Without meaning to sound alarmist I invite you all to bear in mind that, statistically, there is the potential for some people not to mean us well.
‘fraid so, folks.
Remember:
- You are not being paranoid
- There are bad actors out there
- They may possess the intent in trying to manipulate you against your interests
If a person, device or network becomes compromised there is a credible possibility that additional exploitation through extortion, blackmail or other forms of interference may be further down the line… or imminent.
You, your family, colleagues, friends & communities may not be initial end targets, but may instead be more readily comprisable stepping stones towards some other malicious end.
Your digital or information assets, knowledge or connections may prove interesting enough to become targets of opportunity.
Reputations? Finances? The ability to carry out day-to-day work or other transactions? All potentially at risk… so be sure to exercise a degree of caution.
Trust: it’s the name of the game
To be honest all of this is nothing new. I suspect that most students of history, politics & international relations can tell you that espionage, whether international, industrial or corporate, has been a game played across the world stage for centuries.
Arguably phishing or other efforts to compromise individuals and systems are just another iteration of age-old ruses, tricks or cunning contrivances dating back millennia to get one over against an adversary.
And of course there’s always room for plain old-fashioned theft, mischief or just to see whether a thing can be done.
People and their motivations can be fascinating… but their motives don’t necessarily have to make any kind of sense to you.
If you haven’t taken the time recently to say thanks to your IT team, SOC analysts & security specialists, whether in-house or via a service provider, why not take the time to do so?
Go on, they won’t bite. Unless provoked. Much.
Probably best to take snacks…
Stay safe out there.


